Security Awareness briefings for every candidate.
It is important for employers to know and understand that candidate’s background is not filled with unmitigated risk. However, new employees to the organisation might not fully understand or comprehend the employer’s security posture and culture. That’s where a security & cyber awareness mini course comes in. After the Cleard Life suitability interview is complete, our qualified and security cleared vetting officers will spend one-on-one time with each candidate discussing key fundamental elements of information security and cyber security and how they can help to keep their existing or future employer safe. We quickly gauge the candidate’s prior knowledge of security concepts and then test & calibrate their knowledge relating to five popular themes. This helps candidates understand the security environment that they are walking into and also helps the employer comply with and make in-house induction and on-boarding a breeze. We will confirm with the employer at the time of the result that the cyber awareness and security awareness training has been completed.
1. Understanding & applying the need-to-know principle.
The term “need to know” describes the restriction of access to information which is considered very sensitive. Under need-to-know restrictions, even if one has all the necessary approvals to access certain information, one would not be given access to such information unless it is necessary to conduct your work duties.
- Limit your requests for information to that which you have a genuine need-to-know. Be aware that you may be expected to explain why you need to know it.
- Refrain from discussing work-related information where the discussion may be overheard by persons who do not have a need-to-know.
- If someone asks you for information, you are expected to ensure they are cleared appropriately and have a genuine need-to-know before you provide any information to them. It is best practice to talk about this interaction with your security section if you believe that a co-worker has violated the need-to-know principle.
2. Suspicious contacts.
If you are approached by, or communicate with, any individual whose purpose appears to be to obtain from you confidential, Personally Identifiable Information (PII) or other sensitive information, then this is a security concern. You should report the situation and interaction, especially if it is characterised by the acronym SOUP:
- Suspicious
- Ongoing
- Unusual or uninvited
- Persistent
Speak to your supervisor, chain of command and your Security Officer or security section.
3. Locking your computer.
A clear screen policy refers to a practice related to ensuring that sensitive information in digital format is not left unprotected at personal or public workspaces when they are not in use, or when someone leaves their workstation, either for a short time or at the end of the day.
- You can lock your computer by pressing CTRL+ALT+DEL keys or by pressing Windows and L keys simultaneously.
- You unlock your computer by pressing CTRL+ALT+DEL keys simultaneously then entering your username and password.
- Lock your machine every time you are away from it; no matter how long you are gone for.
4. Socially engineered emails.
Spam is the electronic equivalent of junk mail. The term refers to unsolicited bulk, and often unwanted, email, eg. adverts for pharmaceutical products. Phishing emails attempt to collect personal or financial information or attempt to infect your machine with malware (malicious software). Spear phishing emails are highly specialised attacks against a specific person, or a small group, to collect information or gain access to systems. eg. A crafted email with specific and very relevant topic.
- While socially-engineered emails can be highly sophisticated, there are ways to differentiate them from legitimate emails:
- Do you really know who is sending you the email?
- Are you expecting an email from them?
- Is the content of the email relevant to your work?
- Does the email ask you to access a website or open an attachment?
- Is the web address relevant to the content of the email?
- Is the email from a personal email address?
- Is the email suspiciously written?
- Have you received the same email twice?
5. Close of business checks.
Many employers have legal and contractual requirements that demand information protection. A clean desk policy specifies how employees should leave their working space when they leave the office. Most clean desk policies require employees to clear their desks of all paperwork at the end of the day. Here is an example of a workplace lock-up procedure. Ensure that:
- all computer systems are logged off and screens are switched off;
- there is no sensitive information left out in the workplace;
- Laptops and other electronic media storing security classified info are secured;
- there is no PII or sensitive information in wastepaper bins;
- whiteboards and other displays do not show any sensitive information;
- vaults, filing cabinets and other storage containers are locked, and that combination locks are spun off properly;
- windows and doors are locked; and
- keys to filing cabinets or storage containers are secure.
Conclusion
Become a customer today and mention that you would like to take us up on the Cyber Security & Awareness briefing offer.
Take a look at the four levels of assessments we offer here.
Or see if us managing your security clearance needs might be of assistance (The Cleard Plus service includes mandatory Defence’s Security Awareness course and Assessing & Protecting Information course and Quarterly Awareness Updates!).
There will be more DISP Auditors checking for things like this. e.g. Para 2.23 of a recent Defence Subcommittee inquiry report (available here) states ‘At the hearing, Mr West updated the Committee further and described Defence’s layered assurance process, including an annual report from industry with an attached desktop audit, a more in-depth review of 500 industry bodies (DISP Members) every year, and a further 20 to 30 audits every year where Defence has identified requires additional work’).
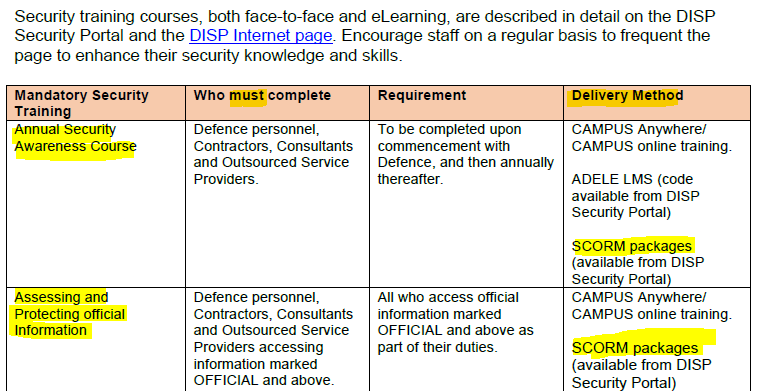
DSPF control 16.1 states that we “ensure and facilitate Defence mandated security education and training courses for Industry Entity personnel engaged in Defence work.”
DISP-Info will refer you to the DISP Security Officer Resource guide, page 25.
We do all of this through our Learning Management System:
Get in touch now to discover more – book a Discovery Call today or visit Cleard Plus.
Former CSO at the World’s Largest Aerospace Company Talks How to Tackle Insider Risk