Exploring what the right cybersecurity path forward looks like when people are involved.
70,604 cyber security professionals were asked to respond to the question, ‘What Keeps You Awake at Night’, with the option to select one of three possible answers.
a. Third Parties
b. Insider Threats
c. Nation State Actors
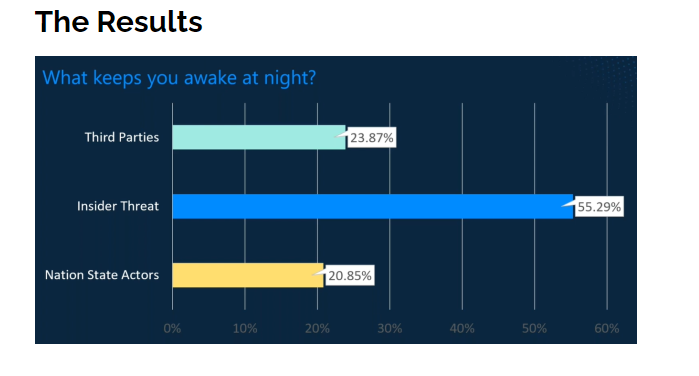
55% of cyber professionals are worried about their own staff, their own colleagues. This echoes what Terry Halvorsen, the former CIO of the US Department of Defense, said in recent Sydney conference: “The single threat to your system is people. Some of it is not even malicious. People ask what keeps me up at night? It’s people.” He then recommended business leaders to spend their cyber budget on people – before tech. That is an important statement from a person who controlled a USD 42 Billion annual
budget.
Background: Low hanging fruit are external people.
The typical corporate network topography is wide and that means a lot of potential entry points if left unsecured or vulnerable. The work from home (WFH) trend has exacerbated
this. The last thing any senior leader needs is the fallout from a major security breach or attack. We are seeing near daily headlines littered with cyber breach incidents and
ransomware of well-known brands. Closer to home they might even be third party supply chain partners.
Internal threats can cost many times more than an external attack.
Cyber professionals are aware that staff are normally, by default, accessing sensitive networks and information from anywhere, for the foreseeable future. The climate in which potential internal breaches – negligence or intentional – is elevated. Tech solutions try to secure all the hardware that the internal user accesses. This is difficult when
trusted employees WFH and use unsecured home computers, home printers, home USB sticks etc. Other tech solutions include user behaviour motioning software to detect and
alert when internal people are in the corporate network system and doing the wrong thing.
The role of trust cybersecurity
No-one doubts that cybersecurity plays a critical role in ensuring overall business continuity and also public facing trust. However, Deloitte’s recent Reputational Risk
survey discovered that the ‘people’ element plays an even more important role than ‘cyber’.

The challenge of people risk in cybersecurity
The greatest risk to organisations remains the human component of security. While it is possible to lock down permissions and track data movement against all programmatic access, ensuring that humans don’t behave maliciously has become an even bigger concern now more than ever.
Someone once said that ‘character is who you are when no one is looking’. When an employee is say for example WFH and no one is looking, will they act ethically and with
integrity. Can they be trusted? The Information Security Manual (ISM P10) states that people must be ‘trusted & vetted’ before having access to ICT systems. The challenge is how do you vet someone’s character for trustworthiness?
Is there an online multiple choice ‘ethical dilemma’ test you can get them to do?
Do you strap candidates up to lie detectors in a dark room with a bright desk lamp in their face?
Consider the value of an ISO 31000-style Risk Assessment
The NSW Independent Commission Against Corruption’s ‘Employee Screening Whitepaper’ points to the Attorney General’s Protective Security Policy Framework (PSPF). The terms ‘trusted’ and ‘vetted’ are coined their and it encourages the use of ISO 31000 risk management principles.
By assessing a person’s background:
* financial considerations (financial stress)
* security attitudes and violations (cyber wilful recklessness)
* criminal history and conduct (including those not disclosed in a police certificate)
Adverse findings in any these areas can have a bearing on character traits such as honesty, trustworthy, tolerance, maturity, loyalty and resiliency. An ISO 31000 people
risk program (sometime called an insider threat management program) not only vets your people but you’ll reduce the people risk and have a reputation of a trusted workforce.
risk program (sometime called an insider threat management program) not only vets your people but you’ll reduce the people risk and have a reputation of a trusted workforce.
Conclusion
Since 2010, we have been entrusted by the Australian government, Fortune 500 companies in Australia and small to medium organisations to provide discreet, timely and accurate screening solutions that support them in making sound, fact-based HR decisions. As a result, we have conducted thousands of one-on-one interviews and verification transactions, tailored to the requirements of the organisations we work with.
Test drive your new employee screening program today – for free – www.cleard.life/join






