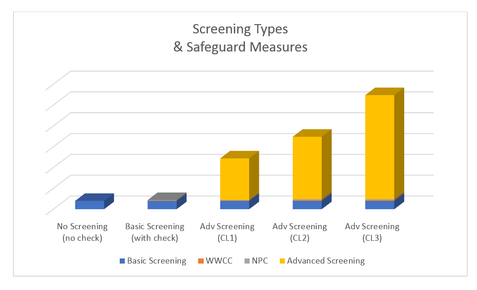
AS 4811:2022 as the Unifying Framework for Workforce Screening in an Era of Balkanised Clearances The proliferation of specialised security clearances and workforce screening requirements—ranging from TOP SECRET national security clearances to sector-specific checks like the Working With Children Check (WWCC), ASIC, Critical Worker Check, MSIC, NDIS worker screening, and Aged Care compliance—has created […]
AGSVA Security Clearances – the Clear Difference. In today’s competitive landscape, many service providers offer generic background screening solutions without a true understanding of—or commitment to—the rigorous requirements of AS4811. At Cleard Life, we set ourselves apart by prioritising the critical standards that truly matter. While competitors may overlook or disregard AS4811, our approach is […]
The relentless compromising of the private sector, which remains a soft but strategic target, has diluted the conventional boundaries of conflict, forcing the government to enhance its posture. Australia is not immune and there is clear recognition that we need to do more to protect our nation against attacks on our critical infrastructure. The Parliamentary […]
How to implement and navigate the Critical Infrastructure Personnel Security Rules. The mandatory Critical Infrastructure Risk Management Plan (CIRMP) for critical infrastructure assets will increase security obligations for Critical Infrastructure Entities & “systems of national significance”. CIRMP obligations will require entities to (a) identify hazards for which there is a “material risk” that the hazard […]
Empowering Education: Leveraging UFIT Protocols for Critical Infrastructure Rule 2 Compliance and DISP Pre-employment Screening In today’s internationally interconnected world, protecting our critical infrastructure is more important than ever. Universities, as centers of learning and innovation, play a crucial role in this landscape. They must adhere to stringent regulations to protect sensitive information and assets. […]
“The whole reason behind having an insider threat program was to change the culture … and at least once a quarter, we would always inject one of our insider threat stories.” The interview with Dave Komendat, former CSO at Boeing, discusses the importance of insider threat programs in changing company culture and ensuring security. He […]
Cyber Security Risk Audits start to look at the HR workforce. A recent study out of Cylab, 69% of respondents had more than 5 malicious, high-concern insider incidents. 44% of businesses had more than 10 incidents. 11% had more than 100 incidents, such as financial fraud, sabotage, data theft, or workplace violence. In 2021 this trend won’t stop. Cyber security is always going to be […]
Exploring what the right cybersecurity path forward looks like when people are involved. 70,604 cyber security professionals were asked to respond to the question, ‘What Keeps You Awake at Night’, with the option to select one of three possible answers. a. Third Parties b. Insider Threats c. Nation State Actors 55% of cyber professionals are worried about their own staff, their own colleagues. This echoes what Terry Halvorsen, the former CIO of the US Department of Defense, said in recent Sydney conference: “The single threat to your system is people. Some of it is not even malicious. People ask what keeps me up at night? It’s people.” He then recommended business leaders to spend their cyber budget on people – before tech. That is an important statement from a person who controlled a USD 42 Billion annual budget. Background: Low hanging fruit are external people. The typical corporate network topography is wide and that means a lot of potential entry points if left unsecured or vulnerable. The work from home (WFH) trend has exacerbated this. The last thing any senior leader needs is the fallout from a major security breach or attack. We are seeing near daily headlines littered with cyber breach incidents and ransomware of well-known brands. Closer to home they might even be third party supply chain partners. Internal threats can cost many times more than an external attack. Cyber professionals are aware that staff are normally, by default, accessing sensitive networks and information from anywhere, for the foreseeable future. The climate in which potential internal breaches – negligence or intentional – is elevated. Tech solutions try to secure all the hardware that the internal user accesses. This is difficult when trusted employees WFH and use unsecured home computers, home printers, home USB sticks etc. Other tech solutions include user behaviour motioning software to detect and alert when internal people are in the corporate network system and doing the wrong thing. The role of trust cybersecurity […]
Facilitating prime and subprime contractor participation in defence projects through expert clearance sponsorship and management. In the rapidly evolving defence sector, securing appropriate security clearances is paramount for both prime contractors and their subcontractors. Cleard Life, a prominent Australian firm specialising in security vetting, provides essential services through its Cleard Plus program to support the […]
Introduction As the global focus sharpens on the security of critical infrastructure, one aspect often remains underrepresented: the potential risks arising from personnel within the supply chain. Members of the Defence Industry Security Program (DISP) have highlighted these concerns, especially when interfacing with the Critical Infrastructure Security Centre (CISC). This article dissects the personnel-related hazards […]
The security expert has three reasons why you should never charge your phone at an airport – Callum Jones (via unilad.com) A security expert has warned tourists against charging their mobile phones at an airport. After many hours of checking directions, seeing where you need to go once you land at your arrival destination, […]
DISP Members and Departments now require an Employee Suitability Check before Requesting a National Security Clearance. The workforce behind the defence force needs to be a trusted workforce. If you are a Security Officer for a Defence Industry Member or a Security Officer in a Department that requires AGSVA security clearances, then you should be […]
Show me Evidence of your Insider Threat Program (ITP). That is a question an aspiring Defence Industry Security Program (DISP) company will be asked. Then a Big 4 consulting firm will more than likely audit this element on your first or second anniversary. Do you know that your Insider Threat Program will need to have […]
1. Introduction With insider threats posing a significant challenge in the Health industry, it is imperative to establish rigorous user screening processes that align with Australian Standard 4811-2022 and Protective Security Policy Framework (PSPF) 12, ensuring the security and integrity of commonwealth systems – such as the My Health Record system. This article highlights the […]
FIVE Recruitment Trends to Watch: 1. Australian Standards for employment screening (AS 4811-2006) was updated, after 15 years, to include adjudication. 2. Critical Infrastructure expanded & positive security obligations (personnel vetting) tightened – covering 1.6+m employees. 3. The expanded Critical Infrastructure sector – Defence Industry – must sponsor & manage their own AGSVA security clearances. […]
You can utilise an MPSSP, like Cleard Plus, to ensure safety and compliance, while enabling your security cleared workforce to focus on more valued projects. You may have heard of a Managed Security Service Provider (MSSP) with a dedicated Security Operations Centre – SOC. Enter Australia’s first dedicated Managed Personnel Security Service Provider, MPSSP. Think […]
Learn how improved reporting by peers, family, and social contacts can help prevent insider attacks and protect your organization’s IT systems and data. Insider threats can pose a significant risk to an organization’s IT systems and data. These threats can come from current or former employees, contractors, or business partners who have authorized access to […]
Mission: To Strengthen Australia’s Integrity for Society’s Betterment Vision: To bring about an unbroken state of affairs, where integrity empowers the performance and prosperity of government, businesses and not-for-profits. Strategy: To strengthen Australia’s national integrity system through faster, cheaper, smarter, better personnel vetting practices which enables the right person to move into the right position […]
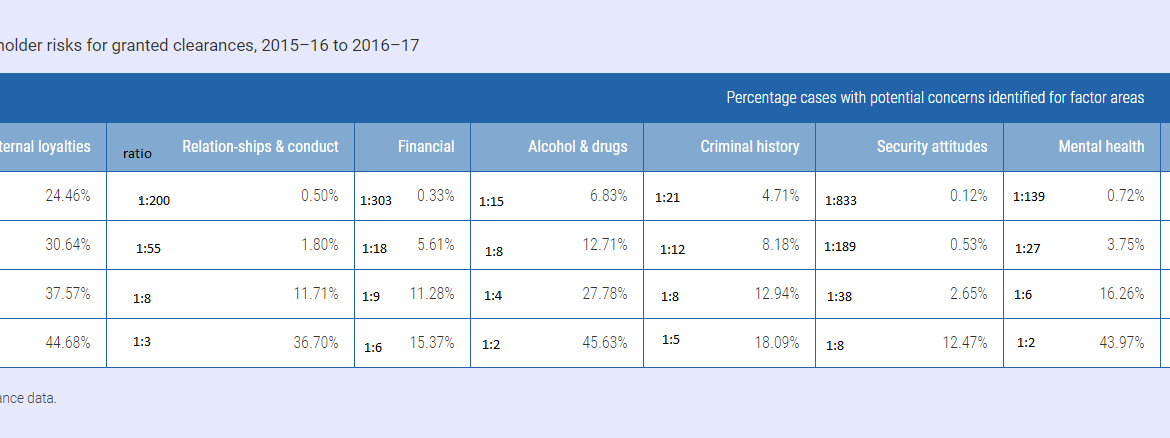
Our Background Suitability Interview Questions relate to: Background & Family structure Education & Employment Personal Relationships Allegiance & Loyalty Substance Use Illegal conduct Emotional health Financial Personal conduct CV Check Which then is filtered through the lens of Attorney General’s Suitability Standards: Guideline A: External loyalties, influences and associations Guideline B: Personal relationships and conduct […]
So what do you guys do, again? Can we ask you a question first? Did you know that employers can experience massive pain when hiring the wrong person? The cost is huge and the pre-employment & rehiring market is a multi-million dollar industry. In some industries, rehiring market it up to 40%. These are costs […]
Vetting the Cleard.life way: The secret sauce. When evaluating a candidate’s suitability, Cleard life considers the information through the lens of the Home Affairs Adjudicative Guidelines (AG). In addition to brief introductory explanations for each guideline, the lists potentially disqualifying conditions and mitigating conditions, which are very useful in evaluating a candidate’s suitability. These guidelines […]
Emerging standards and technology can be used to mitigate people risk in the retail environment and increase the quality of your candidates by 70%. We know how devastating employee theft can be: 30% of business closures blame this. Then there are data breaches. 1 in 4 data breaches are caused by malicious employees (not accidental […]
Critical Infrastructure entities must now hunt for spies. Preemployment screening does not hunt for spies. The PSPF does. We do. Meet Bruce. He works for your critical infrastructure company. He is like many workers in Australia: born in another country, studied at a great university there but then moved here to make a life […]
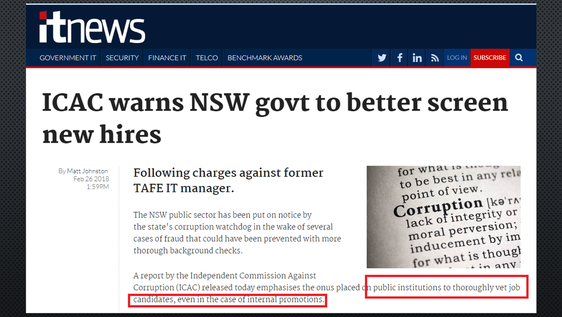
Are Your Personnel Security (PERSEC) Measures AS4811 Suitable? 20% to 30% of job applications contain some form of false information according to a recent report of the NSW Independent Commission Against Corruption (ICAC). Nothing in the report suggests ICAC’s statistics relate solely to NSW or to the public service. Very likely similar issues will be […]
Security Awareness briefings for every candidate. It is important for employers to know and understand that candidate’s background is not filled with unmitigated risk. However, new employees to the organisation might not fully understand or comprehend the employer’s security posture and culture. That’s where a security & cyber awareness mini course comes in. After the […]
A Suitability Assessment Interview (SAI) can take as little as 40 minutes over the phone for the most Basic level assessment (CL0) and perhaps up to four hours for the human-only, highest-level, face-to-face interview (CL3). Our Vetting Officers tell candidates that they will be looking for evidence of qualities such as loyalty, honesty and reliability, […]
A Guide to Australian Standards for Workforce Screening Employment screening processes are beyond the standard interview process done by HR, recruitment companies or the hiring manager. Employment screening requires extensive resources and systems designed to uncover information that the employer requires to make an informed decision about the eligibility and suitability of a candidate – […]
Personnel Security (PERSEC) still remains a challenge for DISP Members. The Defence Industry Security Program normally requires a security clearance at some level to work on defence projects and get access to sensitive information – but not at Entry Level. Recent changes to DISP means that your personnel security measures must include an initial suitability assessment, […]
5 Things To Present and Position Your Company As A Trusted Third-Party Partner Most of the B2B companies look for long term relationships with big companies. It is not an easy job to gain their trust to grab long term contract. Assume a big client of yours’ wants appropriate personnel security measures to be in […]
Personnel screening isn’t just about weeding out untrustworthy individuals or high-risk workers or to reduce the likelihood of counter-productive workplace behaviours from manifesting. For both employee and employer, the goal of pre employment screening is to find a good match for both parties in order to ensure a positive, productive working relationship for everyone. With […]
Trusted insiders are potential, current or former employees or contractors who have legitimate access to information, techniques, technology, assets or premises. Trusted insiders can intentionally or unknowingly assist external parties in conducting activities against the organisation or can commit malicious acts of self-interest. Such action by […]
Primary Source Verification (PSV) is a known as a ‘hard data’ screening process that involves liaising directly with original issuing sources. Hard data are documents that include, but are not limited to, driver’s licences, education degrees, work permits, passports, employment certificates and practice licenses, bankruptcy checks, police checks, credit checks, digital footprint social media check, […]
The Australian Government is developing our nation’s next Cyber Security Strategy as part of its commitment to protecting Australians from cyber threats. The new strategy will be a successor to Australia’s landmark 2016 Cyber Security Strategy, which set out the Government’s 4 year plan to advance and protect our interests online backed by a $230 […]
Your Candidate Has A Criminal Record: Now What? Court Convictions, Disclosable Court Outcomes: Individualised Risk Assessments – the new Australian Standard AS4811 way. Research has found that about most employers do not perform any type of individualised assessment when criminal convictions are present. Therefore an adverse or derogatory Police check “Result” from one of 165 […]
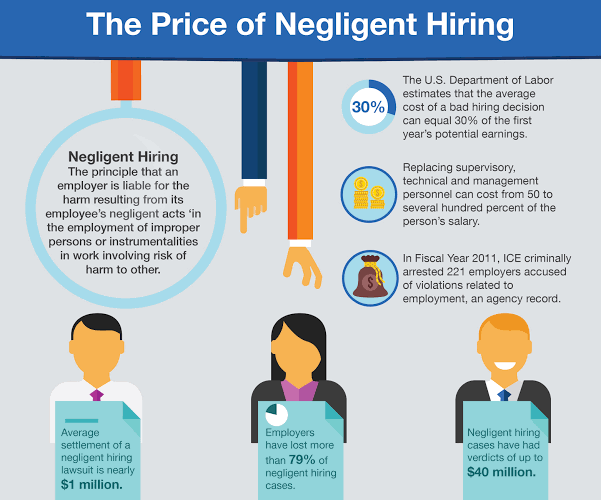
How to Protect Your Company From the Cost of a Bad Hire. How Much Can A Bad Hire Cost Your Company? Why do organisations hire poorly? Luckily, bad hires and the heavy financial burden associated with them can be prevented before they occur. You can: Identify the characteristics of a bad hire BEFORE it happens. […]
Preemployment ‘Best Practice Guide’ for Social Media Screening. A digital footprint is the unique pattern of electronic transactions made by an individual’s publicly accessible online presence. An assessment of an individual’s digital footprint can provide insight into their life, interactions and personal views. This information may identify behaviours of concern or provide further assurance that […]
5 Ways Technology is Changing the Face of HR With ground-breaking HR technology solutions all around us, we’re seeing a tech boom that is fundamentally reshaping the way we work — and how we think about HR. Some of the most interesting — and disruptive — examples are powered by artificial intelligence and automation. AI […]
It is important for any organisation to conduct proper background checks on prospective employees to ensure only the right candidates are hired. Background checks of potential employees can prove to be an eye-opening and useful tool for all types and sizes of business. They can actually help HR with making the right decisions on hiring, […]
Is ignoring a candidate’s digital footprint negligent hiring? Social media screening in the hiring process is now commonplace. We understand its usefulness in protecting employer brand and business reputation. But we’re also aware of its hidden dangers, potential biases, and legal traps. World governments have differing stances on the practice. Some search the internet to […]
Pre-employment screening is one of the essential steps of the hiring process. Conducting these screening procedures can significantly increase the chance of finding a perfect employee for the job. The times when hiring decisions were made solely based on the interview process are long gone. Nowadays, people are relying more and more on pre-employment […]
We saw this in the news recently “The NSW cyber security agency is extending its scope to cover councils and small agencies.” (https://www.governmentnews.com.au/cyber-security-nsw-to-extend-scope-to-councils) “Customer service minister Victor Dominello on Wednesday announced a three-year, $60 […]
When existing staff win a promotion or have a new need to access sensitive information, you are often placing them into more responsible roles which comes with a higher degree of trust. Intuitively, you know that the risk profile of that person just went up. Do you really know that person well enough? Could […]
PRUDENT EMPLOYERS can conduct checks of a candidate’s police/criminal background, drug use, alcohol habits, mental health, litigious conduct (eg. against employers), credit history and other checks and tests prior to making a job offer. However, it is important to ensure that the screening company and their processes comply with the Australian Privacy Principles, anti-discrimination legislation […]
A response to the Child Abuse Royal Commission: a way forward to stop the pain of hiring the wrong person. The Royal Commission’s Final Report relating to human resource management noted that “the nature of religious ministry requires more rigorous screening and selection than for other employees, to ensure that individuals are suitable for their […]
Society demands a higher standard of personnel screening & vetting Inside the recommendations of three Royal Commissions (Sexual abuse, Banking and Aged care) that these sectors require a higher standard of personnel screening & vetting. In other words Society demands a higher level of assurances. Society now trades on trust, but we don’t overtly check […]
COMMENT FROM THE CATCH 22 ARTICLE: “The ENTIRE contracting community would LOVE a “direct to candidate” shop-front from AGSVA, and an elimination of the need to be already placed in a role that requires a security clearance a given level. We’d all be positively vetted. Make security vetting a personal obligation like a white card, […]
Identifying whether interviewee is truthful is one of the biggest challenges to human resource professionals. With the experience gained from screening thousands of candidates, we have identified five markers to identify candidate’s truthfulness which will make your work easier. Observe the following markers in the interview to figure out the truthfulness of the candidate Vague […]
Which Suitability Clearance level is right for your personnel? How do you select the right one? Does everyone in your organisation need the same level? Answer: Great questions. Using a ‘Scope and Effect’ grading methodology, you can self-assess and guide your organisation in classifying the appropriate level to match your personnel risk management. EXTREMELY LOW […]
Occupations and Cleard Life Clearance Levels – a helpful guide. Which Cleard Life Suitability Clearance level is right for your personnel? How do you select the right one? Does everyone in your organisation need the same level? We have used a ‘Scope and Effect’ grading methodology in a previous post to help self-assess and guide […]
Rigorous Employment Screening A Must Stringent compliance obligations for the banking and finance industry mean it is imperative to implement rigorous employee background screening when hiring. As illustrated by recent high profile cases, falsification of employment history is a growing issue across a range of industries. One solution is to use a background checking company, […]
Let’s say that a few days ago, you signed a declaration to say that you are willing to be honest and not mislead the process. Now, that the day has arrived – imagine sitting in front of an Intelligence Officer for a few hours for a chat. It turns out that the ‘Intel Officer’ has […]
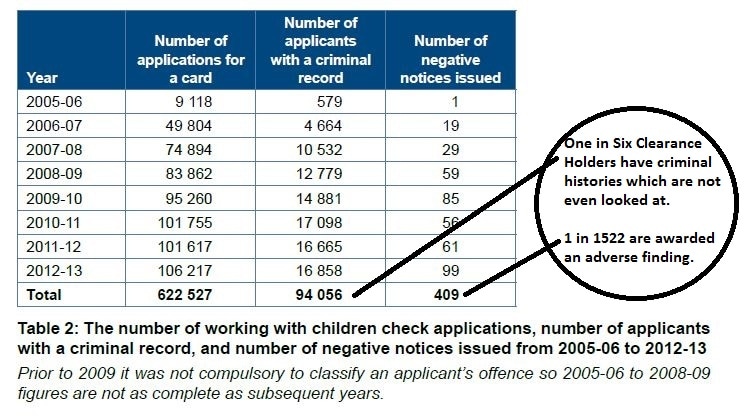
1 in 6 WWCC (Working With Children Card) also known as Blue Card holders have a criminal record! How does that headline make you feel? Surprised, shocked? Should this have your executives worried? If you knew that 1 in 6 of your child-workers had criminal convictions, do you think the parents would feel that your […]
We have served the Commonwealth Government for over 10 years conducting national security clearances up to the highest levels. Our vetting officers are experts in lie detection and screening out people who cannot be trusted based on their background, character and other vulnerabilities. If you have children, we know how concerned parents can be […]
SafeWork Laboratories* forensic toxicologist Andrew Leibie said almost a quarter of a million Australians were high on ice at work “on any given day.” The number of workers testing positive nationally increased from 1:66 in 2016 to 1:52 in 2017, equating to some 240,000 workers nationwide. In safety sensitive industries it is worse: 1:45 workers […]
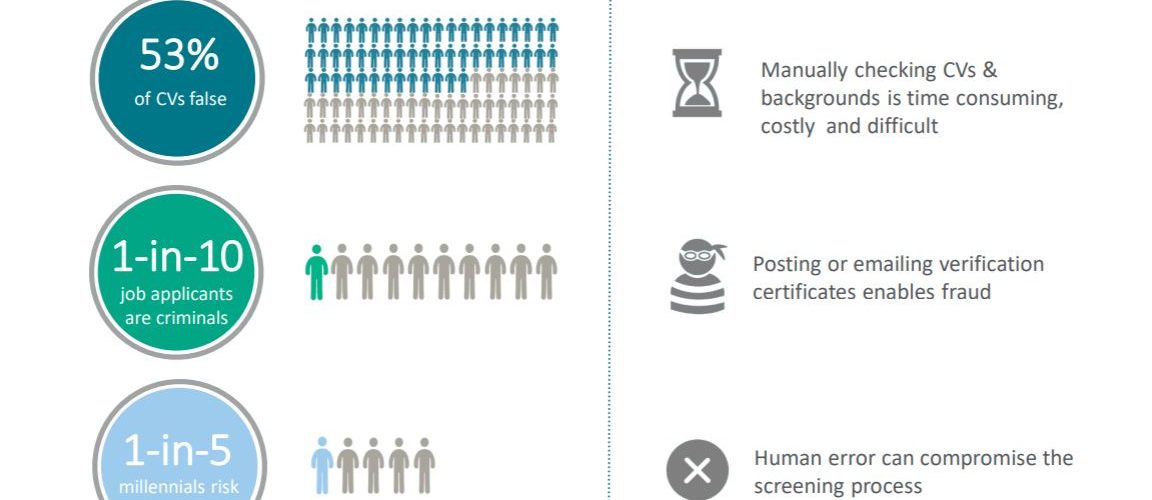
The above info-graphic is an example of a large “QUICK AND EASY” verification company. We do not dispute their facts on the left-hand side. But here is our response to the driving factors: Manually Checking: Cleard.life Response: If 53% of CVs have false or misleading items, then a ‘manual’ check (using real life vetting officers) […]
Guest #1: Our company has been discussing the necessity of obtaining a Police check for successful applicants, as part of our recruitment process. We discussed which roles a Police check should be requested for, and we concluded that whilst support roles, such as finance, HR and technology require trust and responsibility for the Company’s confidential/sensitive data, […]
Q. Do National Police Check (NPC) results show up ALL the results? In short: No. For a small amount of money, you can go to a plethora of websites around 165 companies last count), who promote and process police checks and the result will show “disclosable court outcomes”. Did you notice the qualifier “disclosable”? This […]
Background checks are essential for the trust and safety of an organisation, but is a cheap & fast criminal history check truly enough to ensure that you are doing all you can to prevent workplace risk? Australian Standards 4811 Workforce Screening says ‘no’. Consider the new wave of threats, sometimes called counter-productive workplace behaviours, and […]
Many small business leaders face major issues when choosing their background check options. And the result is often costly. When you’re a small business owner, choosing the right background checking service is a more demanding and difficult task than it is for a huge corporation, which can draw upon dedicated, more expensive resources. This is […]
We saw an article recently about some handy tips before securing a Candidate: “Once you have advertised the position, narrowed down the field and finally identified the perfect candidate, before you make them an offer, here is a check-list of four useful tips to help you through the last important pre-employment screening phase.” 1. Check […]
As a Recruitment Agency, consider how you can stay ahead of the trends and protect your clients. Security, ICT breaches, personal safety, fraud, adverse mental health, financial issues, illegal conduct all risk derailing your recruitment recommendations. We discover hidden risk. Personnel security is fundamental to good business. Most personnel strive to conduct themselves in an […]
Board Member Vetting: A Search for Disqualifying Attributes? While the concept of personnel vetting is usually giving someone a more intense “going over” and is becoming the norm (more than 350,000 public sector personnel have security clearances), vetting should be the standard when it comes to board recruiting. Vetting prospective board members that originate from […]
Are you Naked? Is Cyber Insurance a Must? * 15% of SME’s have cyber insurance. * 1.955 million Australian businesses are not insured. * 70% percent of all businesses are unprepared for a cyber-attack. * 34% of breaches involve malicious internal actors. * 59% of orgs experience at least one malicious insider attack over […]
Kevin Mitnick, famed computer hacker and computer security consultant put it this way: “They may know that they shouldn’t give out certain information, but the fear of not being nice, the fear of appearing ignorant, the fear of a perceived authority figure – all these are triggers, which can be used by a social […]
The need for employee background checks is very well documented and yet 65% of Public Servants do not have an official clearance. However, we expect that most of private and non-profit organisations incorporate, at least at some level, an employee background check in their hiring process. Perhaps it is a Police check, or a credit […]
How Do I Start Getting My People Through A Cleard.life Check? 1. Book a Discovery Meeting with the Team. 2. Discuss your screening requirements to see if we help – we can discuss products, services, process and terms of Service etc. 3. Nominate your Candidates (email, excel spreadsheet, online request form) 4. Receive the Results […]
When it comes to personnel and IT, it’s a high-risk environment right now. 9 in 10 data breaches involve trusted insiders – mainly to due to negligence 1 in 5 data breaches are caused by malicious employees 1 in 5 lie on their job resumes 1 in 5 had misrepresented their qualifications 3 in […]
How many times you have made the final decision to hire a Candidate for a critical role in your company? We know this is one of the hardest jobs to perfect. They say 1 in 4 companies have made a poor hiring decision in the past year and 1 in 3 small businesses fail due […]
3 Ways School Principals Can Reduce the Risk of Child Abuse on their Watch and Comply with Regulations and Ministerial Orders. VICTORIA Education and Training Reform Act 2006 CHILD SAFE STANDARDS – MANAGING THE RISK OF CHILD ABUSE IN SCHOOLS Ministerial Order No. 870 The Minister for Education makes the following Order. Dated 22 December […]
It turns out that a AUD50 police check does not buy a lot of comfort or trust these days. And the sharing economy companies and governments around the world know it. For example, 1 in 9 applicants were rejected. Ouch. Under a new state background check process in Massachusetts, 8,206 people who applied to drive […]
Beyond Merit: Ensuring Suitability in Public Sector Recruitment: How PSPF’s New Screening Requirements are Transforming Hiring Practices If you recruit for the public sector, recent changes mean your hiring process has fundamentally shifted. No longer can you simply recommend the best candidate for a job based solely on merit. Now, you must also assess the […]
Joseph Steinberg is a cybersecurity expert and entrepreneur who founded the information security companies, Green Armor Solutions and SecureMySocial. He invented several popular cybersecurity technologies in use today, writes a column on cybersecurity for Inc., and is the author of several books on information security. Q. “In general, the greatest data security risk is posed […]
The reputation of your industry and your membership organisation is essential to its survival. The trust and confidence the community (industry) will have a direct and profound effect on your organisations’ standing and longevity. Occasionally, member organisations large and small, will need to respond to varying crises to maintain the reputation and standing of the […]
1 in 4 Complaints to the Human Rights Commission are due to Criminal Record Discrimination. Are you next? If you: Refuse jobs to candidates Dismiss Employees Refuse Promotions or Transfers … and some of the process you use to arrive at those decisions are due to the person’s criminal history, then please read on. It […]
Lurking behind every funding or proposal – whether it is a start-up pitch, or a service or product offering – there is an unspoken sentiment: “I don’t really know this person. Who are these people? Are they honest? Are they trustworthy”. Yes a signed confidentiality agreement maybe in place. Yes, you might know of a […]
How to get a Suitability Clearance … for Free. If you are involved in the procurement process for your organisation, you may like to see how our Suitability Clearance can be incorporated into your tender process … at no cost to you. Often, tenderers or contractors to government are only required to have their key […]
What do you mean suitable? We mean suitable as defined by the Attorney General’s Protective Security Policy Framework PSPF12 and PSPF13 and the related Adjudicate Guidelines & associated vetting protocols which includes the whole-of-person concept. Put simply, we look at minimum integrity requirements such as criminal/illegal activity involvement, workplace conduct and any criminal associations. Let’s […]
A Hypothetical one Sided Phone call between friends, goes something like this: Caller A: So, what’s your security strategy? Caller A: What do I mean? Well, IBM says 44.5% of breaches are caused by malicious trusted insiders. Not fat fingers, not clicking on a wrong hyper-link, not accidents, not Russian hackers. Intentional. Caller A: So let me […]
The #1 mistake companies make in hiring temporary workers is … not vetting them as if they will be there permanently. Solution? A Pre-employment screening service especially designed for Temps. We are delighted to have the opportunity to outline a recruitment solution for your temporary workforce that will dramatically reduce reputation loss and hiring risks, […]
Q. Does your internal security program integrate with your contract management process to ensure that third party risks are identified and managed? All organisations should consider supply chain risk management. If a supplier, manufacturer, distributor or retailer (i.e. businesses that constitute a supply chain) are involved in products or services used by an organisation, there […]
Job Interview Questions That You Can’t ask … But We Can. It’s good to know the difference between Recruiters and the Cleard.life Advanced Background Investigation Agency. What you, as a job interviewer, cannot ask: HR Interviewer: What is your marital status? Cleard.life: We can ask, in order to assess Trustworthiness and Loyalty. HR Interviewer: Have you […]
Whether it be the religious NFP sector, the banking and finance sector or the elderly care sector, you will note the significant elements is deficiency in screening processes. Not to say that an overt Integrity check is the silver bullet: a be all & end all to the malevolent employee/volunteer acts done in the workplace […]
CLEARD.LIFE: As a leader in national security clearances, we also have a B2B pre-employment screening solution that can be incorporated into the HR and recruitment process aimed to improve, develop, maintain and create relationships with current and new clients. HR COMPANY: As a global Recruitment and HR Services organisation, we already have internal procedures and […]
There is value to the fact that pre employment background assessments can make your hiring process more efficient by reducing your interview time costs. Rather than assigning a person (or a panel) to spend an hour with each applicant, you can reliably filter out those who aren’t “suitable” before they move to the interview stage. […]
How vetting can augment and supplement the way your organisation reaches membership admission determinations. Membership has its privileges. And members have responsibilities – like ensuring they do not throw the entire organisation (and sometimes the industry) into disrepute. So logically, whoever allows members into the organisation have an even greater responsibility to ensure that the […]
Digital Innovation: Australia’s $315b opportunity. The new report from Alpha Beta for CSIRO/Data61, called “Digital Innovation: Australia’s $315b opportunity” identifies eight strategic areas where Australian businesses can succeed in creating new digital products or services. These opportunities are precision healthcare, digital agriculture, data-driven urban management, cyber-physical security, supply chain integrity, proactive government, legal informatics and […]
The research is in: Criminal History Checks are Futile. A Response to the “Scoping Review: Evaluations of Pre-employment Screening Practices.” by the University of Melbourne. Summary: Basic Screening practices which include basic referee checks and “black mark” database checks are futile. Enhanced Screening must now be the new normal. Research: The effectiveness of criminal background checks, as […]
How #regtech + suitability clearance = PERSEC1 compliance. We are a team suitability experts, engineers and data scientists passionate about building better solutions to stop trusted insiders and counter-productive workplace behaviours from disrupting your workplace, operations and reputation. In this instance, we focus our attention on the #regtech trend and how our solution can apply […]
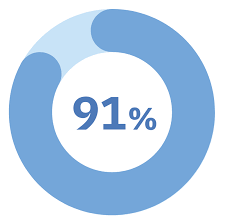
In an Ohio-based Employers Resource Association* survey… 91 percent are using background checks. That seems high. But what s.p.e.c.i.f.i.c.a.l.l.y. does that mean? A Google search? Police check? Facebook search? LinkedIn page view? A 2 minute call to the a previous boss? But more importantly, what do you do when you receive an adverse result? To […]
1 in 4 potential employees admit to behaviours that most employers consider high-risk. HR Managers and Risk Managers need to get onto the same page. Independent university studies have demonstrated the value of integrity tests that screen for hostility, drug and alcohol abuse, theft and lying in the pre-employment phase. But these tests have yet […]
Marc Weaver Databasable is an IT consultancy firm that provides database administration support and specializes in moving your databases and applications into the cloud. Founded by Marc Weaver in 2015, databasable uses his vast employment experience from large financial institutions in London, Sydney, and New York. “Obviously a data security breach from an outsider will result […]
What to consider when selecting a pre-employment screening vendor. Choosing a background screening provider is an important decision that affects your entire organisation, from human resources and security to everyday employee relationships. It is great to have an expert on your side, helping inform important hiring decisions – decisions which affect your organisation’s […]
Our Response to the “NDIS Quality and Safeguarding Framework”. NDIS: How it will work: A nationally consistent screening process will be developed: the results of the screening process for an applicant will be valid throughout Australia, regardless of the state or territory in which it was issued. Cleard.life response: As a national security vetting […]
Many private sector businesses face choices when moving forward with background checks for employees. And the results are too often costly. With the cost of hiring a new employee averaging thousands dollars (8-15% of annual wages), for less than a day’s wage you can get access to 10-fold background check. A bad hire can […]
When Academic Admission Discretion Meets National Security. If you are part of a school that delivers highly specialised courses, which maybe technically UNCLASSIFIED, then know it maybe true that sensitive topics that involve Defence-related topics are crucial and central to the course outcomes and objectives. For example, the Certificate IV in Government (Personnel Security) […]
GREG MANCUSI-UNGARO @BrandProtect Greg Mancusi-Ungaro is responsible for developing and executing the BrandProtect market, marketing, and go-to-market strategy. A passionate evangelist for emerging technologies, business practices, and customer-centricity, Greg has been leading and advising world-class marketing initiatives, teams, and organizations for more than twenty-five years. Prior to joining BrandProtect, Greg served in marketing leadership roles at […]
Troubling research is coming to light concerning the disparity between personnel security ideas and reality. For example (notice the slippery slope as what constitutes good proactive screening): 85% cent have convictions that ‘some’ things should bar employment in their organisation. 1 in 2 (61%) thought police checks ‘essential’ for prudent pre-employment screening 1 in 6 […]
As a leader in national security clearances, we also have a B2B background screening solution that is an Australian standard (4811:2022) can be incorporated into large scale projects and bid proposals. For example, if a Defence Prime requires key management (and staff generally) to hold an AGSVA security clearances (sometimes called an Australian Habilitation) but […]
You invest great effort to get your people to interview several Candidates. You laboriously negotiate with your team to pick your favourite — only to then ask the Candidate for a few references to call. After all this time and effort (which you feel is some type of distraction), you call those references with a […]
A recent survey of companies found that 45% of HR respondents said they screen potential job candidates by perusing their profiles on social media sites such as Facebook and Twitter in search of warning signs that a candidate might not be a good fit. Among the most common reasons cited are: – Candidate posted provocative […]
CHRISTOPHER BURGESS @burgessct Christopher Burgess is the CEO, President and co-founder of Prevendra. He is an author, speaker, advisor, consultant, and advocate for effective security strategies, be they for your company, home, or family. “The most serious threat to a company’s data security is the…” Insider threat, which comes in two forms: The malevolent insider is […]
When to ask for a criminal record check For most jobs, a criminal record check should be requested only from short-listed applicants or from those invited to interview. This minimises: unnecessary and time-consuming administration involved with processing many consent to disclosure forms the expense, as police services charge for the police checking service the risk […]
STEVE DURBIN @stevedurbin Steve Durbin is Managing Director of the Information Security Forum (ISF). His main areas of focus include the emerging security threat landscape, cyber security, BYOD, the cloud, and social media across both the corporate and personal environments. Previously, he was Senior Vice President at Gartner. “As data breaches increase, many will be the […]
A Response to the Royal Commission on Banking: Credit Verification process can be done easily and quickly. COMMISSION: “You don’t do anything to verify what the broker tells you about the customer’s expenses, you don’t do anything to check that the information accurately represents the customer’s living expenses?” BANKER: “Their general living expenses, […]
JAMES GOODNOW @JamesGoodnow James Goodnow is a brilliant, creative, compassionate attorney and a technology aficionado in Phoenix, Arizona who’s been named one of America’s Techiest Lawyers by the ABA Journal, the official publication of the American Bar Association. Apple actually selected him as the first lawyer to be featured in one of its commercials, and also […]
Among 874 incidents, as reported by companies to the Ponemon Institute for its recent Cost of Data Breach Study, 568 (65%) were caused by employee or contractor negligence; 85 (10%) by outsiders using stolen credentials; and 191 (22%) by malicious employees and criminals. Data breach cost per breach $2.5 million. The report goes on to […]
Pre-employment screening service We are delighted to have the opportunity to outline a recruitment solution that will dramatically reduce hiring risks, while not interrupting your recruitment processes, and complete the vetting assessments in the fastest time possible. Although we have not yet been able to customise our response to your specific hiring needs and requirements. […]
Frank Russo, senior vice president of risk and legal affairs and privacy officer for Irvine, California-based elder care firm Silverado, is always on the lookout for creative ways to mitigate risk. So he was intrigued when he read the “staggering” results featured in a university study about integrity testing. He began exploring how the […]
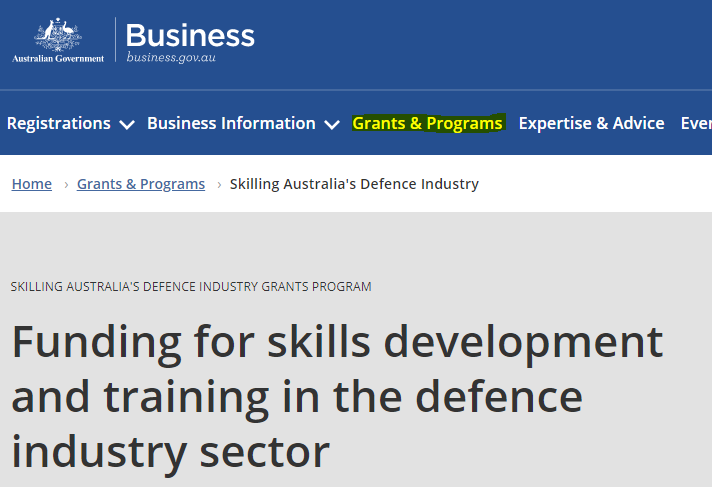
The Skilling Australia’s Defence Industry Grants Program will provide you up to $500,000 over three years to help develop and enhance your defence sector skills and human resources practices and training plans. This is aimed at reducing the personnel security barriers you face and can help you establish enhanced human resources practices and training […]
There are serious consequences of non-compliance. Where an organisation breaches a mandatory notification requirement, the contravention is deemed to be an ‘interference with the privacy of an individual.’ As a result, it may amount to a breach of a civil penalty provision of the Privacy Act. This could result in the organisation being liable for […]