The Australian Government is developing our nation’s next Cyber Security Strategy as part of its commitment to protecting Australians from cyber threats.
The new strategy will be a successor to Australia’s landmark 2016 Cyber Security Strategy, which set out the Government’s 4 year plan to advance and protect our interests online backed by a $230 million investment.
The 2020 Cyber Security Strategy will build on this investment to position Australia to meet the rapidly evolving cyber threat environment.
“The scheme should screen”. Why a Cyber Security Accreditation or Certification scheme needs to include personnel suitability assessments.
Because People matter. Trusted Insiders matter.
Insiders have access to sensitive information on a regular basis and can know how that information is protected. If they want to steal it or leak it they can usually do so with far greater ease than outsiders. Insiders can put an organisation’s data at risk with little effort.
OAIC: “Any sizeable organisation is likely to have some employees who are unhappy at work – meaning that there may be people who have access to data and who have a motive for leaking it.”
An insider with malicious intent who works for or with the organisation has already bypassed most security features without having to do anything but simply log on. 47 Security Experts weigh in the topic of insiders here.
The problem is real. Counter-productive workplace behaviours and hostile acts happen.
Why does a civilian suitability clearance inside a Cyber Security Accreditation or Certification scheme make sense?
Research has proven that a limited, one-dimensional National Police Check is futile to safeguard organisations. Best practices embed enhanced personnel vetting measures (such as background suitability interviews and assessments) into the management of employees, temporary staff and third parties (contractors, partners, and other service or product solution providers).
Having a proven trusted workforce dovetails with the requirements set forth in the Protective Security Policy Framework (PSPF) which recommends screening people for suitability even before offering the job.
OAIC: “Such a scheme could help to rebalance the information asymmetry and risk between individuals and providers of ICT products and services particularly as effective cyber protection is complex and evolving.”
Accenture “One of the growing risks of cyber security is insider threat … through a process of vetting, businesses and individuals could become accredited as a trusted capability partner”.
OAIC: ‘A cyber security accreditation or certification scheme could assist individuals to differentiate the cyber security expertise and credentials of software services, infrastructure and internet platform providers”
Here is how it could work:
- The cyber security organisation applies for cyber security accreditation or certification scheme.
- The accreditors assess personnel security in the following way: the organisation provides evidence that all their people have been awarded either a
- (a) PSPF-compliant government security clearance (eg. Baseline, NV1, NV2, PV clearance) or
- (b) PSPF-compliant civilian suitability clearance
- The accreditor can audit the civilian vetting agency’s process, analysis and clearance results to ensure PSPF compliance and that natural justice, procedural fairness and the whole-of-person protocol has been followed.
Cleard Life Vetting Agency discovers hidden risk and gives the cyber industry a standardised result and piece of mind for all. It is one enabler to meet cyber strategy’s goals.
CLVA is the only PSPF-compliant civilian suitability clearance in Australia.
We can deliver results as fast as next day – not weeks, months and years and is priced as low as $135 per assessment.
CLVA’s “Vetting As A Service” platform:
- Discourages Candidate’s with something to hide.
- Demonstrates your priorities towards security.
- Uncovers falsified or “puffed” credentials.
- Eliminates uncertainties in the hiring process.
- Demonstrates due diligence.
- Encourages Candidate’s to be honest and truthful.
- Saves money & time spent on recruiting, hiring, re-hiring and training.
- Can help protect against negligent hiring lawsuits.
- Reduces chance of injury to employees.
- Reduces employee theft.
- Reduces turnover.
- Reduces workplace violence.
- Reduces insurance premiums.
- Increases productivity and employee morale.
Conclusion:
You don’t have to wait for an accreditation body to be stood up before creating a trusted workforce – talk to use today about how we can assist your goals.
Appendix A
QUOTES FROM THE CYBER STRATEGY 2020 SUBMISSIONS (12% of submissions mention this topic in their submissions)
This is not rocket science. Most breaches are through people, some organisations will quote this stat at being over 90%. So that means good engaging awareness training, and then ensuring a culture of awareness in organisations.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-2.pdf
If an employee gains authorised access to a network and uses it for malicious purposes, this is a personnel security issue. This is a point that was somewhat overlooked in Australia’s Cyber Security Strategy 2016. All security areas are equally important for organisations to consider.
Office of the Victoria Information Commissioner
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-211.pdf
Currently only perceived as a requirement for government agencies to adhere, the Protective Security Policy Frame (PSPF) [PSPF 12 = PERSEC]…. provides a means to address security gaps within private organisations. There is no direction or advice to business to comply with these controls, independent of their dealing with government. Promoting the implementation of these controls will begin to address this need. Improve security clearance procedures to offer faster service and to build a pipeline of multi-classification workforce which can be enacted on short notice.
Deakin University
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-183.pdf
One of the growing risks of cyber security is insider threat: the risks that current or past employees with access to critical cyber security information may pose a malicious threat. A model similar to the Department of Home Affairs’ ‘Trusted Trader’ may be a useful paradigm to consider. Through a process of government vetting, businesses and individuals could become accredited as a trusted capability partner.
Accenture
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-189.pdf
To overcome these constraints, the Australian government could consider setting up a trusted vendor program – in a similar way that the trusted trader program exists with border industries importers. After vetting and under strict controls, more sensitive information can then be shared by Government to help industry counter cyber-attacks or develop better capabilities.
Unisys
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-93.pdf
In recent times there has been a continuous evolution of policy, as the Protective Security Policy Framework (PSPF) has shifted focus from whole-of-government to whole-of-economy. The emphasis is for the PSPF to be supported and taken up by small and medium enterprises (SMEs) and the broader industry, which has not proven to be effective as there is no obvious or demonstrable return of investment for commercial entities, despite Government advice around the increasing threat landscape. … The most commonly identified constraints [to the development of talent] is related to obtaining and maintaining security clearances. The process of obtaining clearances is often long and laborious, it is confusing for those who have never held a clearance.
Lockheed Martin
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-208.pdf
What are the constraints to information sharing between Government and industry on cyber threats and vulnerabilities? A simplified security “clearance” for this particular purpose could be considered on both permanent and temporary/as needed bases.
ACS
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-105.pdf
… an all-of-economy approach to the FY2020 cyber strategy should not ignore the convergence between the military domain and the non-military domain.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-16.pdf
Are there any barriers currently preventing the growth of the cyber insurance market in Australia? If so, how can they be addressed? Two barriers; trust and cost. The recent Banking Royal Commission highlighted the lack of trust of insurance companies generally in Australia, unfortunately for good reason.
[comment: Three RC recommendations include better screening practices]
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-18.pdf
UWA believes that the Government should consider the pros and cons of introducing a set of cyber hygiene obligations that is based on industry standards and best practices.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-22.pdf
Refers to Protective Security Policy Framework (PSPF) & AS 4811 – Employment Screening
Standards Australia
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-90.pdf
… develop the local Cybersecurity Industry – in the same way that we have a local Defence Industry to support Defence projects around the country.
[DISP includes personnel security assessments for non-security cleared staff].
AVA Group
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-103.pdf
Minimum personnel vetting to the same levels across industry and therefore ensuring that sensitive data/information doesn’t find its way to someone that it shouldn’t.
Queensland Government Cyber Security Unit
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-33.pdf
What are the constraints to information sharing between Government and industry on cyber threats and vulnerabilities? Lack of security professionals with the correct clearance levels. Pathway for security professionals who are not working in the public sector, to receive levels of clearance commensurate with information they need to receive to inform their organisations of risk.
REA GROUP
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-51.pdf
… allow industry to qualify and hold and share sensitive information.
RSA
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-80.pdf
… our organisations are only as strong as their weakest link. The latest NDB data breach analysis shows that a high proportion of data breaches were due to human error. Therefore, it is not only about having cyber security technology to mitigate data breaches.
iA Group
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-95.pdf
The essential feature of a well-conceived assessment of cyber risk incorporates a whole-of-government and a whole-of-society response. The risk is society-wide and so must be the response.
[comment: three Royal Commission are reflecting society’s standards for trust, which all have recommended enhanced screening for honesty and trustworthiness.]
Flinders University
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-98.pdf
Key vulnerabilities and risks: Privileged Access Management.
Department of Transport (WA)
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-101.pdf
With the increased connectivity and explosion in computing capability, malicious actors of all types –[including] insiders – have more opportunities and greater incentive to identify and exploit vulnerabilities, and employees have more opportunities to make mistakes.
Oracle
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-104.pdf
It is clear that the Government is seeking to gauge the level of support for expansion of its powers to deter, detect and respond to serious cyber threats.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-112.pdf
Ultimately, cyber is about people. People make mistakes; they can act with malicious intent.
Cyber Institute, The Australian National University
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-157.pdf
Recommends AS 4811 – Employment Screening & the Protective Security Policy Framework.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-158.pdf
Australian Government agencies must act consistently with the policies of the Australian Government, such as the Attorney General’s Protective Security Policy Framework.
OAIC
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-197.pdf
Improvements could be made for more trusted forums, perhaps with “Chatham House” rules, for industry to safely voice their experiences in.
Transurban
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-199.pdf
To maintain trust from the Australian community, we recommend that the government ensure there is some form of declaration that all workers with any access to personal information must sign to say that states that neither they, nor any member of their family, or any close friend or associate of theirs:
has had any allegations of sexual or family violence made against them
have never had an intervention order taken out against them.
are not on the sexual offenders register
have never been charged with any form of sexual violence or family violence
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-11.pdf
Providing a free inspection service to SMEs. A one-day audit of their actual operational processes and a vulnerability scan of their systems. 70% of data breaches occur from human factors, accidental or malicious.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-6.pdf
The Notifiable Data Breaches Statistics Report: 1 April to 30 June 2019 highlighted that 42% of the notified breaches involved financial details and 62% of the attacks were malicious or criminal. Add to that 34% being related to human error and you make the case for compliance mandates by legislative instrument.
https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-strategy-2020/submission-12.pdf
Appendix B
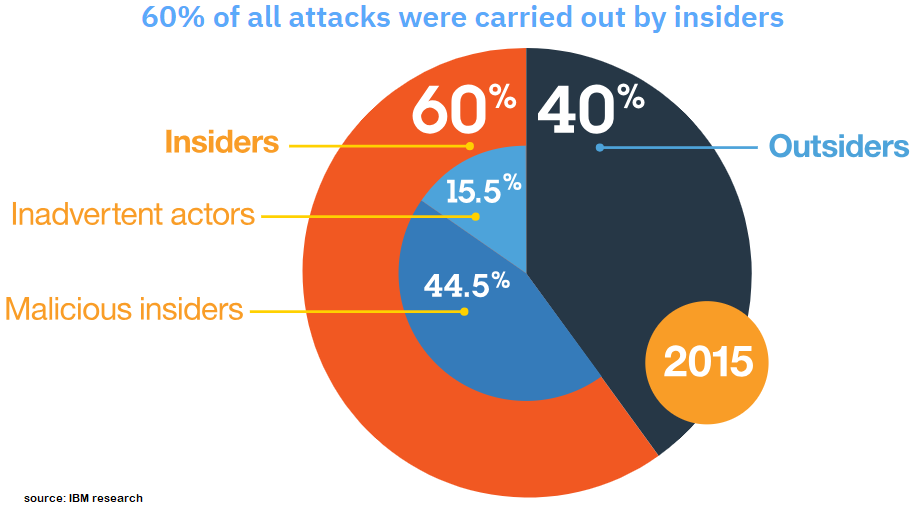
IBM Research about trusted insiders:
Appendix C
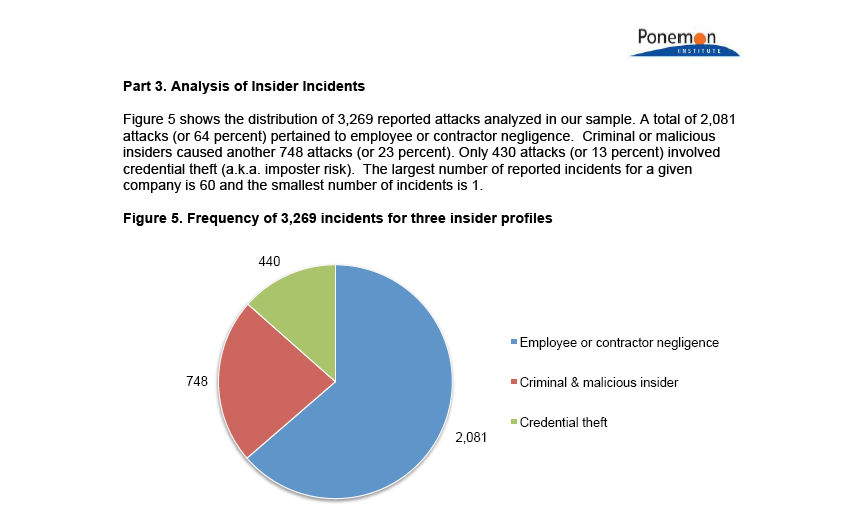
Ponemon research has trusted insiders causing 23% of all breaches.
Appendix D
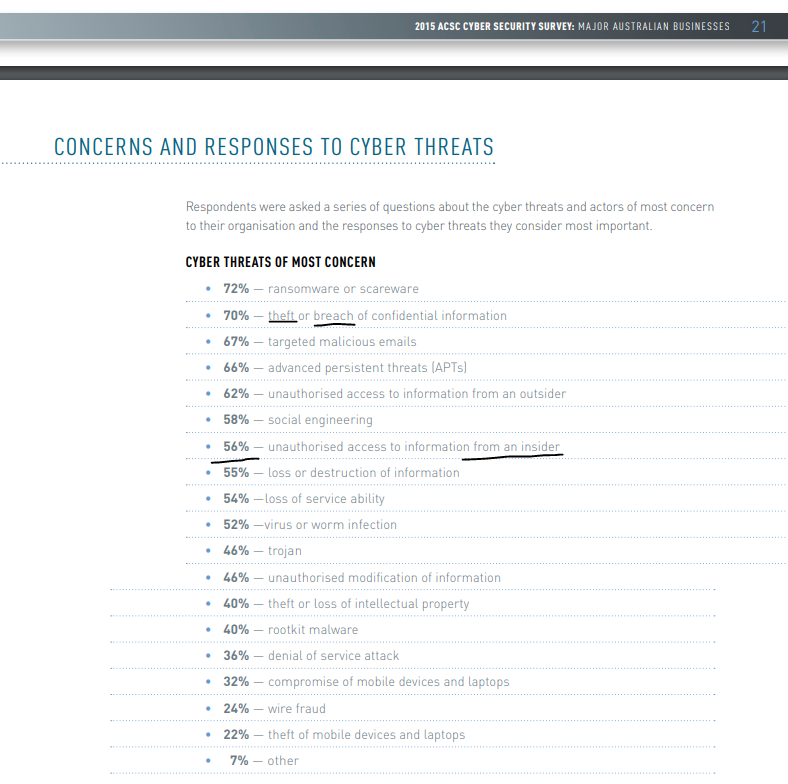
From ACSC’s own research:
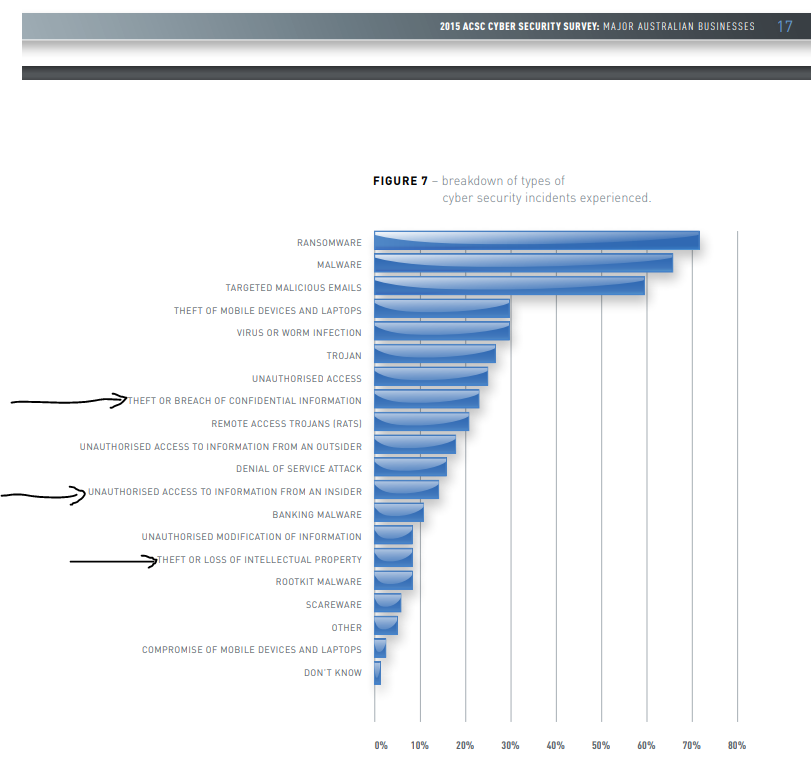

Appendix E
From the Privacy Commissioner:
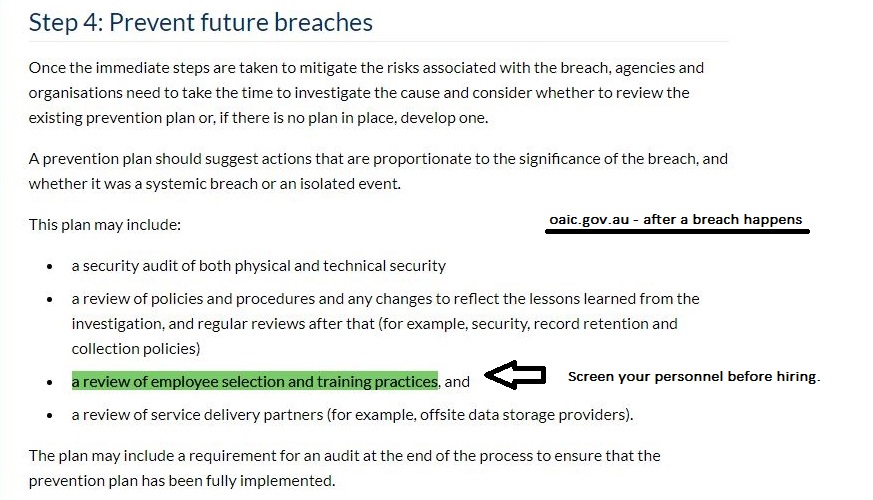
Appendix F
Booz Allen Hamilton as an IT consulting firm commenced its own internal continuous vetting program late 2019. That is how important they view this issue.
Booz Allen’s Sharon Claridge: Continuous Evaluation Program Puts Focus on ‘Trusted Workforce’
Booz Allen Hamilton has implemented a new approach to evaluating its workforce as the government continues to update its security clearance and employee vetting procedures, Federal News Network reported Friday.
Launched over the past year, Booz Allen’s continuous evaluation program covers a range of factors such as financial and personal challenges faced by the firm’s over 27K employees.
Sharon Claridge, director of security services at Booz Allen, told the publication that the initiative serves as a “heavy lift” on the company’s communication, transparency and change management strategy.
“That’s what I’m most proud of, because our interests are a little bit different from the government’s,” she said. “It’s not about continuing eligibility for a clearance, although it is to some good degree. It’s about making sure we’re delivering a trusted workforce to our clients and that we’re taking care of our people.”
Appendix G
Actual words of the PSPF:


Appendix H
The PSPF explanation on how suitability is determined.

Appendix I
The PSPF now explains the necessary character traits:

Appendix J
The PSPF showing what areas of a person’s like needs to be reviewed in order to satisfy suitability:

Appendix K
How CLVA compares to AGSVA (via Australian National Audit Office, ANAO):
Only 1 in 1131 turns complex – however a lot of work (data points, interviews and analysis) goes into this prior to the case turning complex.
‘Complex’ is the polite way to describe a case that has been awarded a withhold or rescind, initially. 792 days delay for a complex case is way too long to wait to work. 697 days is too long. 640 days is too long. 145 days is too long to make a decision.
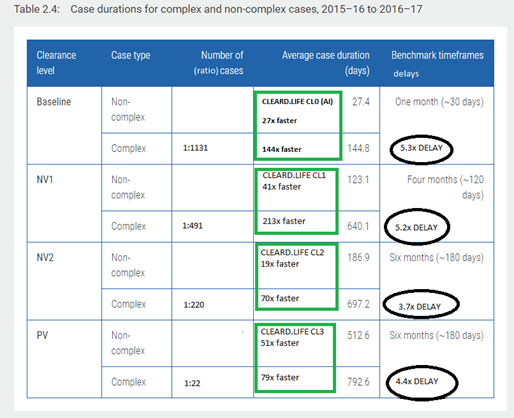
Appendix L
There’s how it works in practice:
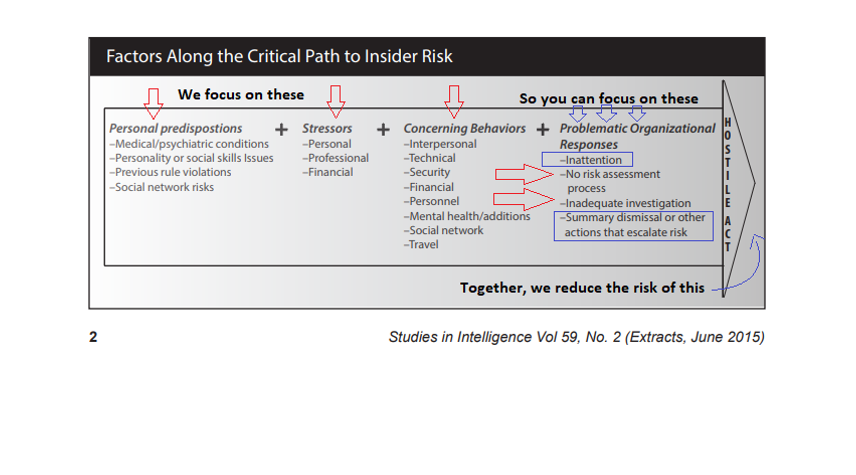
Appendix M
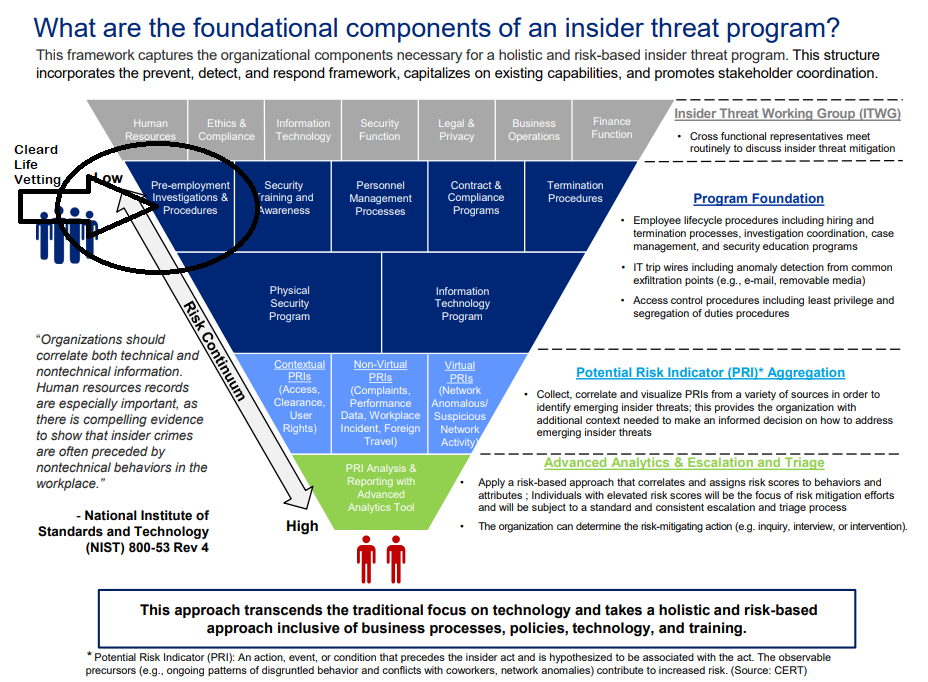
Here is a model to use to set up an Insider Threat Program